Adidas Originals NFT Drop Postmortem

Adidas recently partnered with popular NFT brands gmoney, Bored Ape Yacht Club, and PUNKS Comics to release a collection of NFTs called "Into The Metaverse". For their mint, Adidas set a limit of two NFTs per address, yet someone managed to mint 330 tokens in one singular transaction.
In this research paper I will take a look at the transaction that was used to mint these tokens as well as the Adidas' code that was exploited.
Minting
Within Adidas' smart contract code, we can find the purchase(){...} function which performs a check to see if the msg.sender has minted more than maxTxPublic tokens, 2 in this case. After making this check, _purchase(){...} is called, which performs some more simple checks before minting the token.
1 function purchase(uint256 amount) external payable whenNotPaused {
2 require(block.timestamp >= purchaseWindowOpens && block.timestamp <= purchaseWindowCloses, "Purchase: window closed");
3 require(purchaseTxs[msg.sender] < maxTxPublic , "max tx amount exceeded");
4
5 _purchase(amount);
6
7 }
8 function _purchase(uint256 amount) private {
9 require(amount > 0 && amount <= maxPerTx, "Purchase: amount prohibited");
10 require(totalSupply(0) + amount <= MAX_SUPPLY, "Purchase: Max supply reached");
11 require(msg.value == amount * mintPrice, "Purchase: Incorrect payment");
12
13 purchaseTxs[msg.sender] += 1;
14
15 _mint(msg.sender, 0, amount, "");
16 emit Purchased(0, msg.sender, amount);
17 }From this section of code, we can see that there is no prevention from contracts minting tokens.
This flaw in the minting system was taken advantage of by notchefbob.eth, who created and deployed 165 contract addresses in a singular transaction, which then minted 2 NFTs each before transferring them out and self destructing.
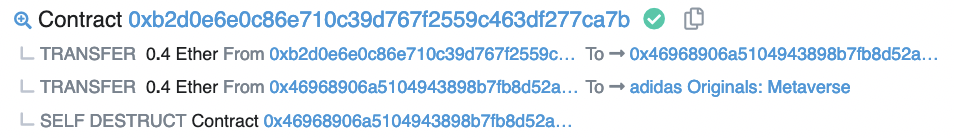
After paying for all 330 NFTs, including gas fees, this singular transaction cost an astounding 93.39 Ethereum. At a current floor price of 0.851 Ethereum, however, this user has unrealized gains of over 190 Ethereum.
Fixing the Contract
In order to prevent this sort of thing from happening in the future, NFT minting drops should have checks to ensure that the minting addresses are not contract addresses. There are a few methods to doing this, which I will explore below.
-
Checking EXTCODESIZE
Ethereum has a built-in OPCODE for checking the bytecode size of an external address called
EXTCODESIZE. While normal Ethereum addresses have bytecode sizes of0, all contracts will have a non-zero value, as long as they are not in the constructor.- This alone cannot completely prevent contract interaction. Contracts that are still within their constructor will return a
0value for theirEXTCODESIZE, and will appear like an address.
- This alone cannot completely prevent contract interaction. Contracts that are still within their constructor will return a
-
Using tx.origin
You can also use the following statement to prevent contracts from interacting with your code.
snippet.sol1require(msg.sender == tx.origin)This can lead to some security issues, but will prevent contracts from interacting with your contract. While
msg.senderrefers to the immediate sender,tx.originrefers to the account that started the transaction. If these two variables do not match, then it is safe to assume that you're dealing with a contract.
After implementing these changes, the resulting code becomes:
1 modifier isNotContract (address _addr){
2 uint len;
3 assembly {
4 len := extcodesize(_addr)
5 }
6 require(len == 0, "Purchase: Account is not an EOA");
7 _;
8 }
9
10 function purchase(uint256 amount) external payable whenNotPaused isNotContract {
11 require(block.timestamp >= purchaseWindowOpens && block.timestamp <= purchaseWindowCloses, "Purchase: window closed");
12 require(msg.sender == tx.origin, "Purchase: Account is not an EOA");
13 require(purchaseTxs[msg.sender] < maxTxPublic , "max tx amount exceeded");
14
15 _purchase(amount);
16
17 }
18 function _purchase(uint256 amount) private {
19 require(amount > 0 && amount <= maxPerTx, "Purchase: amount prohibited");
20 require(totalSupply(0) + amount <= MAX_SUPPLY, "Purchase: Max supply reached");
21 require(msg.value == amount * mintPrice, "Purchase: Incorrect payment");
22
23 purchaseTxs[msg.sender] += 1;
24
25 _mint(msg.sender, 0, amount, "");
26 emit Purchased(0, msg.sender, amount);
27 }Resources & Citations
- Adidas Steps Into the Metaverse by Partnering With NFT Projects Bored Ape Yacht Club, Punks Comic https://news.bitcoin.com
- Solidity Documentation https://docs.soliditylang.org/
- Various Ethereum Transactions [notchefbob.eth, mint transaction, "Adidas: Into The Metaverse"]